请注意,本文编写于 212 天前,最后修改于 212 天前,其中某些信息可能已经过时。
最近在玩Burp suit,用来分析网站数据交互,逆向啥的,爬虫还有渗透,没有什么东西测试,尝试访问自家路由器,小米路由器
ipconfig查看网关
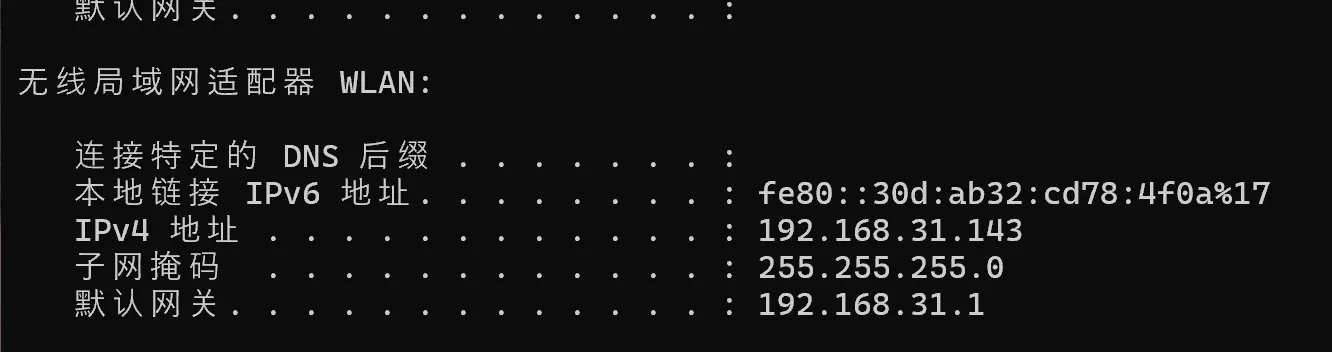
然后直接分析,nmap 192.168.31.0/24
shellC:\Users\zyh16>nmap 192.168.31.0/24 Starting Nmap 7.80 ( https://nmap.org ) at 2025-01-18 17:18 ?D1ú±ê×?ê±?? Nmap scan report for XiaoQiang (192.168.31.1) Host is up (0.032s latency). Not shown: 993 closed ports PORT STATE SERVICE 53/tcp open domain 80/tcp filtered http 8192/tcp open sophos 8193/tcp open sophos 8383/tcp open m2mservices 8443/tcp open https-alt 8899/tcp open ospf-lite MAC Address: A4:39:B3:16:C9:12 (Unknown) Nmap scan report for 192.168.31.32 Host is up (0.0032s latency). All 1000 scanned ports on 192.168.31.32 are closed MAC Address: FA:F9:29:9B:AA:93 (Unknown) Nmap scan report for 192.168.31.78 Host is up (0.014s latency). All 1000 scanned ports on 192.168.31.78 are closed MAC Address: D2:1E:F5:F9:30:47 (Unknown) Nmap scan report for 192.168.31.143 Host is up (0.00s latency). Not shown: 995 closed ports PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds 902/tcp open iss-realsecure 912/tcp open apex-mesh Nmap done: 256 IP addresses (4 hosts up) scanned in 5.86 seconds
拿到了所有链接该wifi的设备
我们的目标是路由器
使用nmap -O ip,nmap -sV ip分析
shellC:\Users\zyh16>nmap -O 192.168.31.1 Starting Nmap 7.80 ( https://nmap.org ) at 2025-01-18 17:22 ?D1ú±ê×?ê±?? Nmap scan report for XiaoQiang (192.168.31.1) Host is up (0.00061s latency). Not shown: 993 closed ports PORT STATE SERVICE 53/tcp open domain 80/tcp open http 8192/tcp open sophos 8193/tcp open sophos 8383/tcp open m2mservices 8443/tcp open https-alt 8899/tcp open ospf-lite MAC Address: A4:39:B3:16:C9:12 (Unknown) No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=1/18%OT=53%CT=1%CU=44371%PV=Y%DS=1%DC=D%G=Y%M=A439B3%T OS:M=678B72CA%P=i686-pc-windows-windows)SEQ(SP=0%GCD=0%ISR=0%TI=Z%CI=Z%II=I OS:%TS=7)SEQ(CI=Z%II=I)OPS(O1=M5B4ST11NW3%O2=M5B4ST11NW3%O3=M5B4NNT11NW3%O4 OS:=M5B4ST11NW3%O5=M5B4ST11NW3%O6=M5B4ST11)WIN(W1=3890%W2=3890%W3=3890%W4=3 OS:890%W5=3890%W6=3890)ECN(R=Y%DF=Y%T=40%W=3908%O=M5B4NNSNW3%CC=N%Q=)T1(R=Y OS:%DF=Y%T=40%S=A%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A% OS:A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y% OS:DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164%UN= OS:0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S) Network Distance: 1 hop OS detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 14.27 seconds
得不到更详细的信息,往下看
shellC:\Users\zyh16>nmap -sV 192.168.31.1 Starting Nmap 7.80 ( https://nmap.org ) at 2025-01-18 17:23 ?D1ú±ê×?ê±?? Nmap scan report for XiaoQiang (192.168.31.1) Host is up (0.000046s latency). Not shown: 993 closed ports PORT STATE SERVICE VERSION 53/tcp open domain dnsmasq 2.71 80/tcp open http nginx 8192/tcp open http nginx 8193/tcp open http nginx 8383/tcp open http nginx 8443/tcp open http nginx 8899/tcp open http nginx MAC Address: A4:39:B3:16:C9:12 (Unknown) Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 13.88 seconds C:\Users\zyh16>
随便访问一个端口,发现是运行了好几个一样的客户端,不知道什么原因,容错吗,接下来访问一下登录,毕竟咱什么也不懂
上BP,
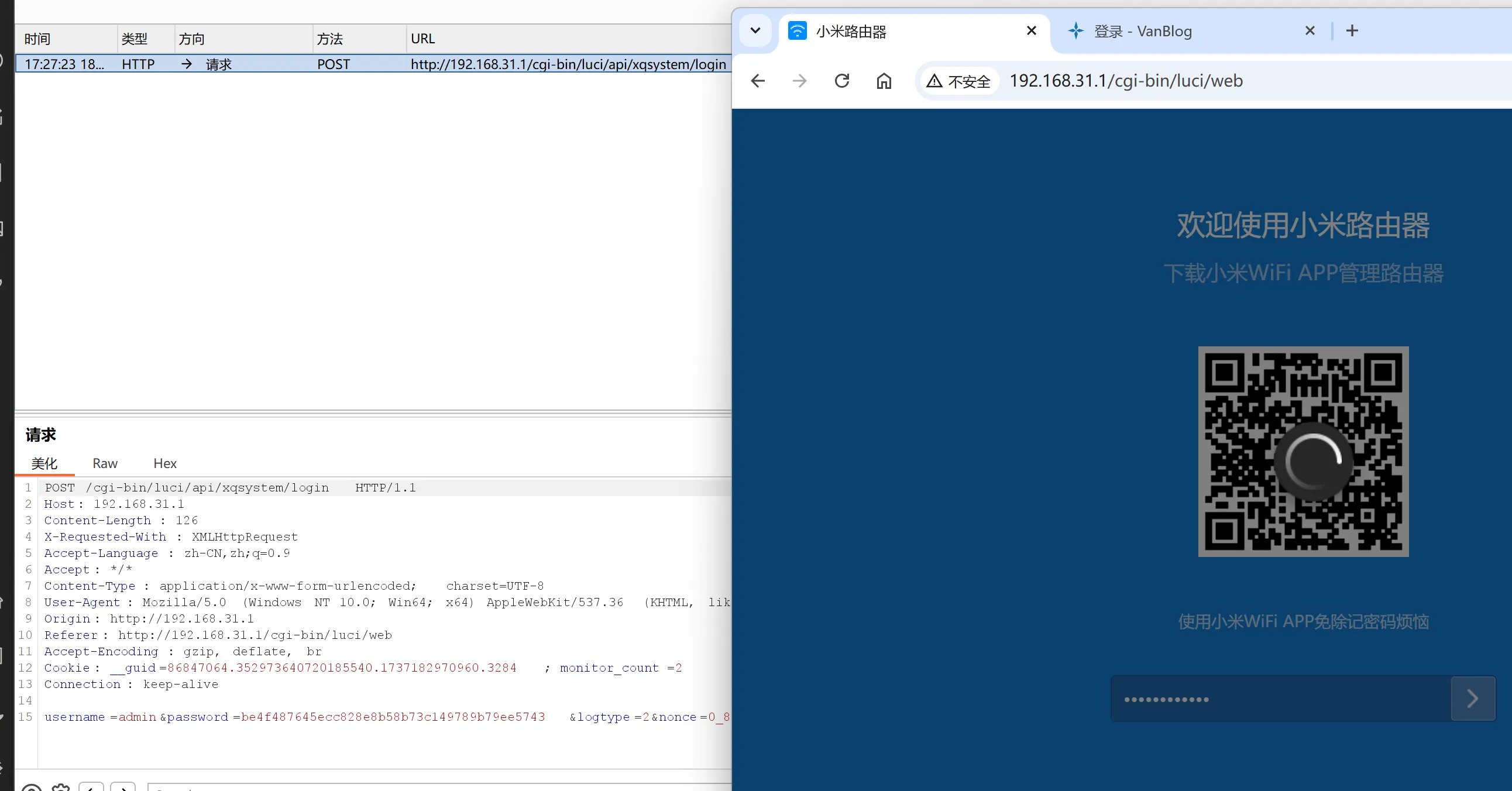
随便输个密码拦截一下
请求
POST /cgi-bin/luci/api/xqsystem/login HTTP/1.1 Host: 192.168.31.1 Content-Length: 126 X-Requested-With: XMLHttpRequest Accept-Language: zh-CN,zh;q=0.9 Accept: */* Content-Type: application/x-www-form-urlencoded; charset=UTF-8 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.6723.70 Safari/537.36 Origin: http://192.168.31.1 Referer: http://192.168.31.1/cgi-bin/luci/web Accept-Encoding: gzip, deflate, br Cookie: __guid=86847064.352973640720185540.1737182970960.3284; monitor_count=2 Connection: keep-alive username=admin&password=be4f487645ecc828e8b58b73c149789b79ee5743&logtype=2&nonce=0_8c%3Ae9%3Aee%3Ade%3A61%3A24_1737192442_7143
这个登录逻辑nonce应该是生成用于保证幂等或者别的什么的,只能用一次的字符串,暂时还不清楚,看密码,前端加密传过去,好办,翻代码,看密码长度像sha1,自己找个网站试了一下不像 后面这个nonce老手可能一眼就看出来可能是盐了,但我是新手,只能翻代码
搜索function login相关的
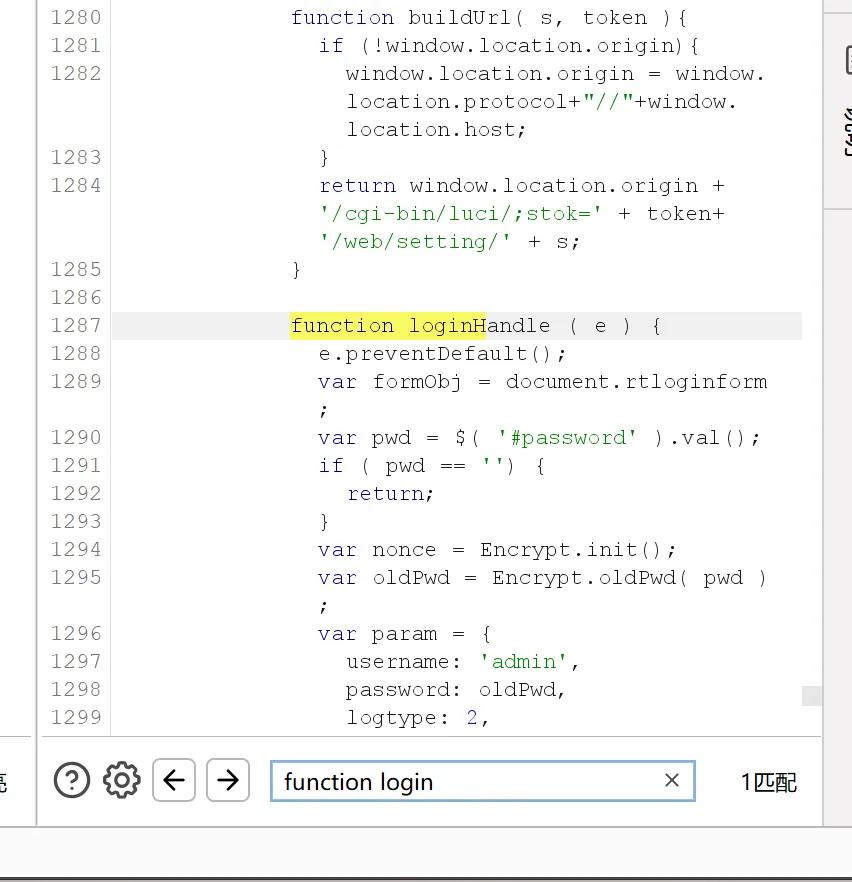
完整代码
js function loginHandle ( e ) {
e.preventDefault();
var formObj = document.rtloginform;
var pwd = $( '#password' ).val();
if ( pwd == '') {
return;
}
var nonce = Encrypt.init();
var oldPwd = Encrypt.oldPwd( pwd );
var param = {
username: 'admin',
password: oldPwd,
logtype: 2,
nonce: nonce
};
$.pub('loading:start');
var url = '/cgi-bin/luci/api/xqsystem/login';
$.post( url, param, function( rsp ) {
$.pub('loading:stop');
var rsp = $.parseJSON( rsp );
if ( rsp.code == 0 ) {
var redirect,
token = rsp.token;
if ( /action=wan/.test(location.href) ) {
redirect = buildUrl('wan', token);
} else if ( /action=lannetset/.test(location.href) ) {
redirect = buildUrl('lannetset', token);
} else {
redirect = rsp.url;
}
window.location.href = redirect;
} else if ( rsp.code == 403 ) {
window.location.reload();
} else {
pwdErrorCount ++;
var errMsg = '密码错误';
if (pwdErrorCount >= 4) {
errMsg = '多次密码错误,将禁止继续尝试';
}
Valid.fail( document.getElementById('password'), errMsg, false);
$( formObj )
.addClass( 'shake animated' )
.one( 'webkitAnimationEnd mozAnimationEnd MSAnimationEnd oanimationend animationend', function(){
$('#password').focus();
$( this ).removeClass('shake animated');
} );
}
});
}
加密过程
jsvar nonce = Encrypt.init();
var oldPwd = Encrypt.oldPwd( pwd );
var param = {
username: 'admin',
password: oldPwd,
logtype: 2,
nonce: nonce
};
接下来需要把这个加密工具对象拔出来,直接搜方法名
jsvar Encrypt = {
key: 'a2ffa5c9be07488bbb04a3a47d3c5f6a',
iv: '64175472480004614961023454661220',
nonce: null,
init: function(){
var nonce = this.nonceCreat();
this.nonce = nonce;
return this.nonce;
},
nonceCreat: function(){
var type = 0;
var deviceId = '8c:e9:ee:de:61:24';
var time = Math.floor(new Date().getTime() / 1000);
var random = Math.floor(Math.random() * 10000);
return [type, deviceId, time, random].join('_');
},
oldPwd : function(pwd){
return CryptoJS.SHA1(this.nonce + CryptoJS.SHA1(pwd + this.key).toString()).toString();
},
newPwd: function(pwd, newpwd){
var key = CryptoJS.SHA1(pwd + this.key).toString();
key = CryptoJS.enc.Hex.parse(key).toString();
key = key.substr(0, 32);
key = CryptoJS.enc.Hex.parse(key);
var password = CryptoJS.SHA1(newpwd + this.key).toString();
var iv = CryptoJS.enc.Hex.parse(this.iv);
var aes = CryptoJS.AES.encrypt(
password,
key,
{iv: iv, mode: CryptoJS.mode.CBC, padding: CryptoJS.pad.Pkcs7 }
).toString();
return aes;
}
};
到这整个加密过程被扒出来了
,接下来尝试用go还原加密过程,看看和拦截到的是不是一样 输入密码123456,拦截到
username=admin&password=18568a99082996cf802d26ceb548090eef74c574&logtype=2&nonce=0_8c%3Ae9%3Aee%3Ade%3A61%3A24_1737193552_5123
记住,nonce要更他一样
zyh16@qwm MINGW64 /d/GoProS/manty $ go run test.go Nonce: 0_8c:e9:ee:de:61:24_1737193552_5123 Encrypted Password: 18568a99082996cf802d26ceb548090eef74c574 zyh16@qwm MINGW64 /d/GoProS/manty
生成的一样
接下来尝试用go去登录
完整代码
gopackage main
import (
"crypto/sha1"
"encoding/hex"
"fmt"
"io/ioutil"
"math/rand"
"net/http"
"net/url"
"strings"
"time"
)
// Encrypt 结构体
type Encrypt struct {
Key string // 固定的 key
IV string // 固定的 iv
Nonce string // 动态生成的 nonce
}
// 初始化 Encrypt
func NewEncrypt() *Encrypt {
return &Encrypt{
Key: "a2ffa5c9be07488bbb04a3a47d3c5f6a",
IV: "64175472480004614961023454661220",
}
}
// 生成 nonce
func (e *Encrypt) Init() string {
e.Nonce = e.nonceCreat()
return e.Nonce
}
// 生成 nonce 的逻辑
func (e *Encrypt) nonceCreat() string {
typeVal := 0
deviceID := "8c:e9:ee:de:61:24"
timestamp := time.Now().Unix() // 当前时间戳(秒)
random := rand.Intn(10000) // 随机数
return fmt.Sprintf("%d_%s_%d_%d", typeVal, deviceID, timestamp, random)
}
// 加密密码
func (e *Encrypt) OldPwd(pwd string) string {
// 第一步:计算 SHA1(pwd + key)
step1 := sha1.Sum([]byte(pwd + e.Key))
step1Hex := hex.EncodeToString(step1[:])
// 第二步:计算 SHA1(nonce + step1Hex)
step2 := sha1.Sum([]byte(e.Nonce + step1Hex))
step2Hex := hex.EncodeToString(step2[:])
return step2Hex
}
// 发送登录请求
func sendLoginRequest(nonce, encryptedPwd string) {
// 构造请求参数
data := url.Values{}
data.Set("username", "admin")
data.Set("password", encryptedPwd)
data.Set("logtype", "2")
data.Set("nonce", nonce)
// 构造请求
req, err := http.NewRequest("POST", "http://192.168.31.1/cgi-bin/luci/api/xqsystem/login", strings.NewReader(data.Encode()))
if err != nil {
fmt.Println("Error creating request:", err)
return
}
// 设置请求头
req.Header.Set("Host", "192.168.31.1")
req.Header.Set("Content-Type", "application/x-www-form-urlencoded; charset=UTF-8")
req.Header.Set("X-Requested-With", "XMLHttpRequest")
req.Header.Set("User-Agent", "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.6723.70 Safari/537.36")
req.Header.Set("Referer", "http://192.168.31.1/cgi-bin/luci/web")
req.Header.Set("Accept-Language", "zh-CN,zh;q=0.9")
req.Header.Set("Accept", "*/*")
req.Header.Set("Connection", "keep-alive")
// 发送请求
client := &http.Client{}
resp, err := client.Do(req)
if err != nil {
fmt.Println("Error sending request:", err)
return
}
defer resp.Body.Close()
body, err := ioutil.ReadAll(resp.Body)
if err != nil {
fmt.Println("Error reading response body:", err)
return
}
fmt.Println("Response Body:", string(body))
// 输出响应
fmt.Println("Response Status:", resp.Status)
fmt.Println("Response Headers:", resp.Header)
}
func main() {
// 初始化 Encrypt
encrypt := NewEncrypt()
// 生成 nonce
nonce := encrypt.Init()
fmt.Println("Nonce:", nonce)
// 加密密码
pwd := "zhang.123" // 用户输入的密码
oldPwd := encrypt.OldPwd(pwd)
fmt.Println("Encrypted Password:", oldPwd)
// 发送登录请求
sendLoginRequest(nonce, oldPwd)
}
成功
gozyh16@qwm MINGW64 /d/GoProS/manty
$ go run test.go
Nonce: 0_8c:e9:ee:de:61:24_1737193824_9494
Encrypted Password: 7088cf0d28cccd73aafe7df63eae915adb8fd5d0
Response Body: {"url":"/cgi-bin/luci/;stok=5f6548ea094bee92b0ac55e770125cad/web/home","token":"5f6548ea094bee92b0ac55e770125cad","code":0}
Response Status: 200 OK
Response Headers: map[Cache-Control:[no-cache] Content-Length:[123] Content-Type:[text/html; charset=utf-8] Date:[Sat, 18 Jan 2025 09:50:22 GMT] Expires:[Thu, 01 Jan 1970 00:00:01 GMT] Micgi-Client-Ip:[192.168.31.143] Micgi-Host:[192.168.31.1] Micgi-Http-Host:[192.168.31.1] Micgi-Preload:[no] Micgi-Server-Ip:[192.168.31.1] Micgi-Server-Port:[80] Micgi-Status:[CGI] Micgi-Switch:[1 1] Server:[nginx] Set-Cookie:[psp=admin|||2|||0;path=/;]]
zyh16@qwm MINGW64 /d/GoProS/manty
$
后续想尝试爆破,但是失败了,连续请求多次接口耗时逐渐增加,应该是进行速率限制了
本文作者:yowayimono
本文链接:
版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!