请注意,本文编写于 205 天前,最后修改于 205 天前,其中某些信息可能已经过时。
最近在写一个自己用的Agent小助手,需要写一些Tools,需要获取ip地理位置和天气信息,这个用开源的IP2REGION很简单,但是因为是自己用的所有不在乎可用性,想起有很多不用登录能在线获取ip的网站,扒别人的接口用
寻找目标
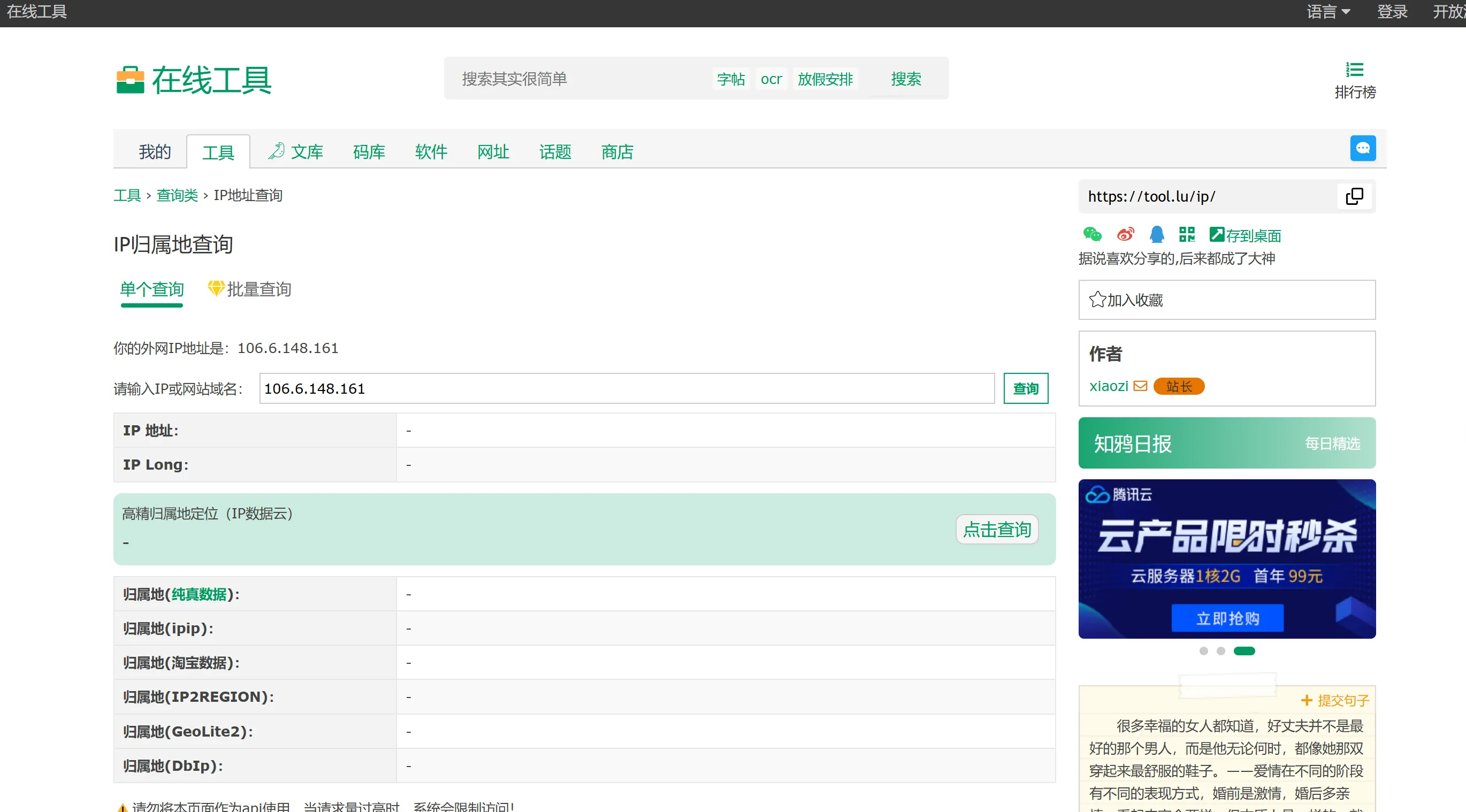
然后一顿分析,目标接口
HTTP/2 200 OK Server: nginx Date: Sat, 25 Jan 2025 12:46:38 GMT Content-Type: application/json Vary: Accept-Encoding X-Ratelimit-Limit: 10 X-Ratelimit-Remaining: 9 Set-Cookie: _session=%7B%22slim.flash%22%3A%5B%5D%7D; path=/; expires=Sat, 25-Jan-2025 13:06:38 UTC; HttpOnly Content-Security-Policy: upgrade-insecure-requests Content-Security-Policy-Report-Only: default-src *; script-src 'self' 'unsafe-inline' 'unsafe-eval' *.tool.lu *.baidu.com *.bdstatic.com; object-src 'none'; style-src 'self' 'unsafe-inline' 'unsafe-eval' *.tool.lu *.baidu.com; img-src 'self' data: *.tool.lu *.href.lu *.baidu.com; media-src 'none'; child-src 'self' *.tool.lu; font-src *.tool.lu *.alicdn.com; connect-src 'self' *.tool.lu *.baidu.com *.alicdn.com; report-uri //a.tool.lu/csp X-Content-Type-Options: nosniff X-Xss-Protection: 1; mode=block Strict-Transport-Security: max-age=31536000; includeSubdomains; preload X-Ua-Compatible: IE=Edge X-Request-Id: ada98ee91ab38240e1e28734eeae9df9 X-Request-Start: 1737809198.592 X-Backend-Server: izbp1bddlmdujhv83mreflz {"status":true,"message":"","text":{"ip":"106.6.148.161","l":1778816161,"chunzhen":"\u4e2d\u56fd \u6c5f\u897f \u5357\u660c \u7535\u4fe1","taobao":"\u4e2d\u56fd \u6c5f\u897f \u8d63\u5dde \u7535\u4fe1","ipip":"\u4e2d\u56fd \u6c5f\u897f \u8d63\u5dde -","ip2region":"\u4e2d\u56fd \u6c5f\u897f\u7701 \u8d63\u5dde\u5e02 \u7535\u4fe1","geolite":"China Jiangxi Ganzhou -","dbip":"China Jiangxi Ganzhou -","ipDataCloud":"\u4e2d\u56fd \u6c5f\u897f \u8d63\u5dde \u4fe1\u4e30 \u5609\u5b9a\u9547","amap":null}}
这里虚晃一招,一时没看出来,解码之后是这样
{ "status": true, "message": "", "text": { "ip": "106.6.148.161", "l": 1778816161, "chunzhen": "中国 江西 南昌 电信", "taobao": "中国 江西 赣州 电信", "ipip": "中国 江西 赣州 -", "ip2region": "中国 江西省 赣州市 电信", "geolite": "China Jiangxi Ganzhou -", "dbip": "China Jiangxi Ganzhou -", "ipDataCloud": "中国 江西 赣州 信丰 嘉定镇", "amap": null } }
好了这就是目标 分析请求
POST /ip/ajax.html HTTP/2 Host: tool.lu Cookie: _session=%7B%22slim.flash%22%3A%5B%5D%7D; uuid=0bf84ab8-3b29-45b3-93f4-942f4588cad9; Hm_lvt_0fba23df1ee7ec49af558fb29456f532=1737805584; HMACCOUNT=293F62AF50E6FA79; _access=728d5abbdbd02720445179f38fb11f35c8471a0d00271247f81a61029ead0c7d; Hm_lpvt_0fba23df1ee7ec49af558fb29456f532=1737809198 Content-Length: 16 Sec-Ch-Ua-Platform: "Windows" Accept-Language: zh-CN,zh;q=0.9 Sec-Ch-Ua: "Not?A_Brand";v="99", "Chromium";v="130" Sec-Ch-Ua-Mobile: ?0 X-Requested-With: XMLHttpRequest User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.6723.70 Safari/537.36 Accept: application/json, text/javascript, */*; q=0.01 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 Origin: https://tool.lu Sec-Fetch-Site: same-origin Sec-Fetch-Mode: cors Sec-Fetch-Dest: empty Referer: https://tool.lu/ip/ Accept-Encoding: gzip, deflate, br Priority: u=1, i ip=106.6.148.161
目标很明确需要获取ip然后构造cookie再进行请求,不然爆403,本着不写接口的初衷,获取ip的接口也扒一下,一顿搜索,找到一个返回ip的html
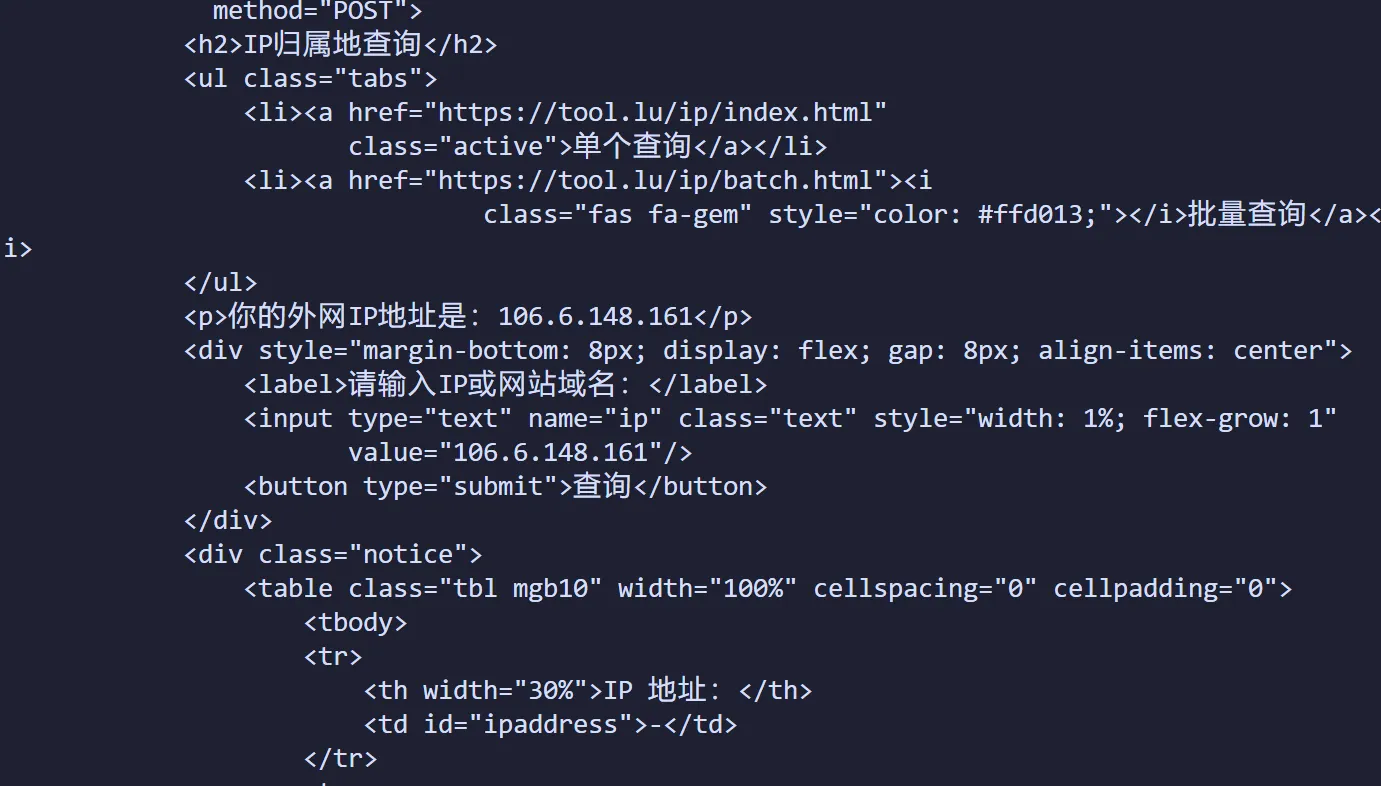
前面有段文本,直接正则匹配一下
这个接口原来带了Cookie,一顿删删减减发现不用,虚晃一招,接下来有一顿删删减减发现只需要_session,uuid,_access三个就好,把返回这些cookie的接口扒出来就好了,人力搜索
最后
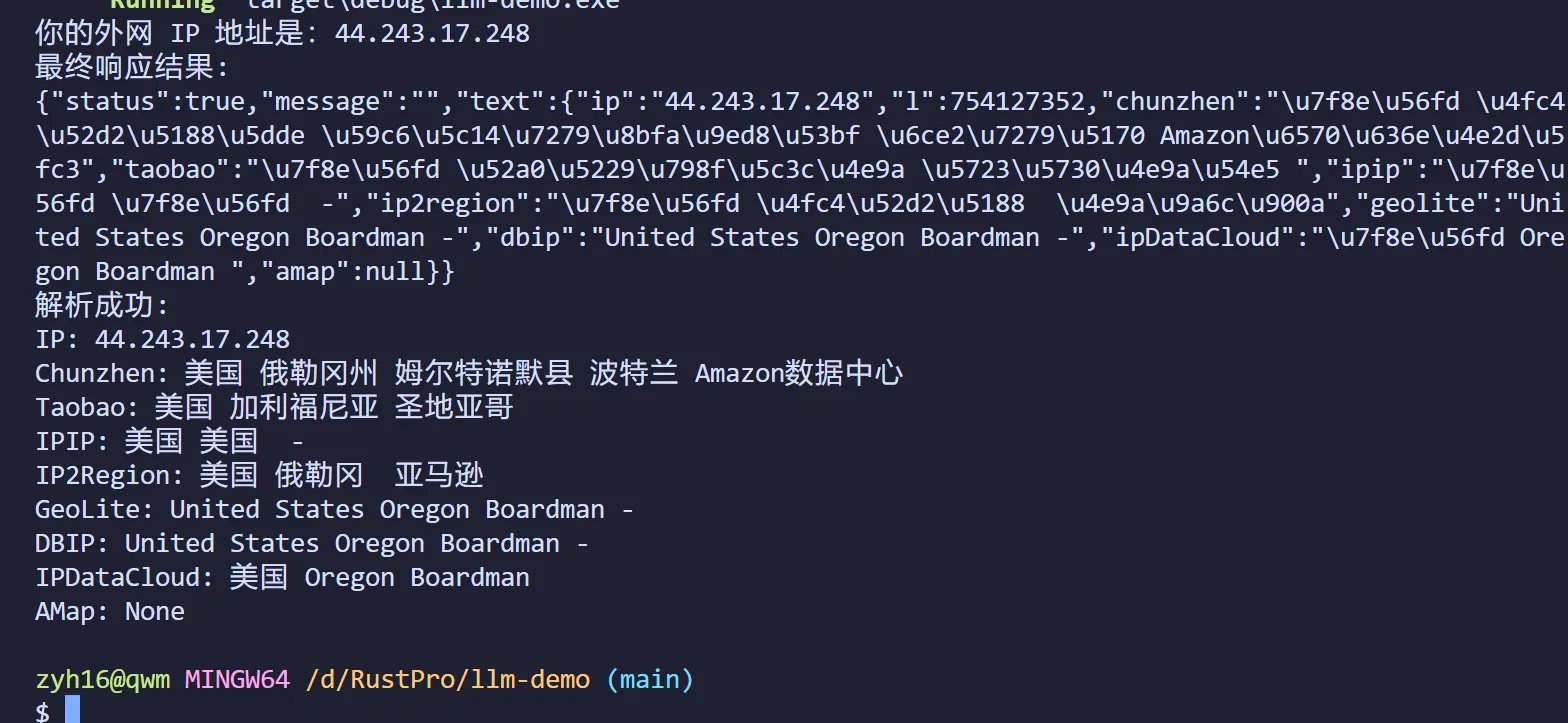 魔高一丈
魔高一丈
本文作者:yowayimono
本文链接:
版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!